Remediate Credential Vulnerabilities
Cybercriminals can leverage stolen credentials to compromise corporate systems, commit theft, and implant malicious software and ransomware to networks. In data breaches, over 60% of these crimes occur with compromised password credentials.
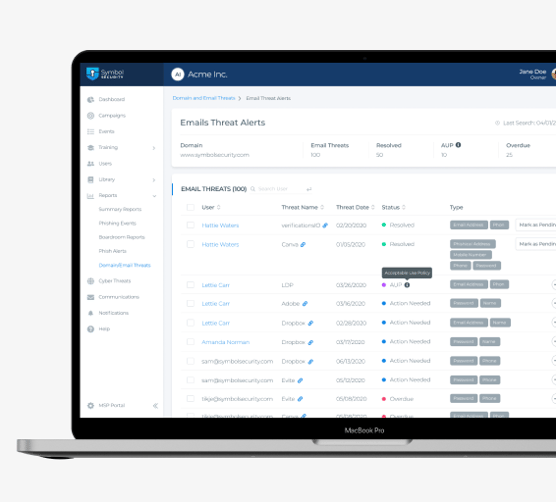
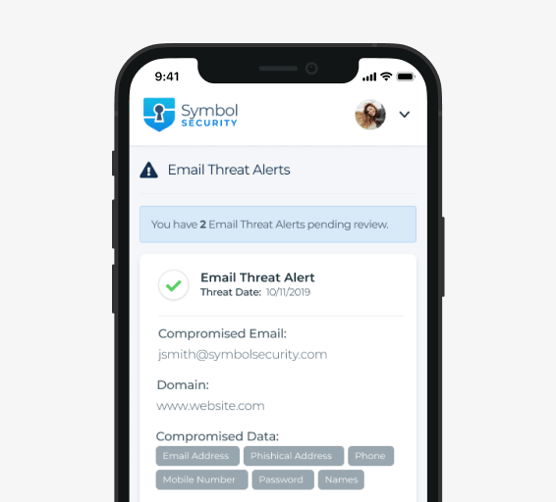
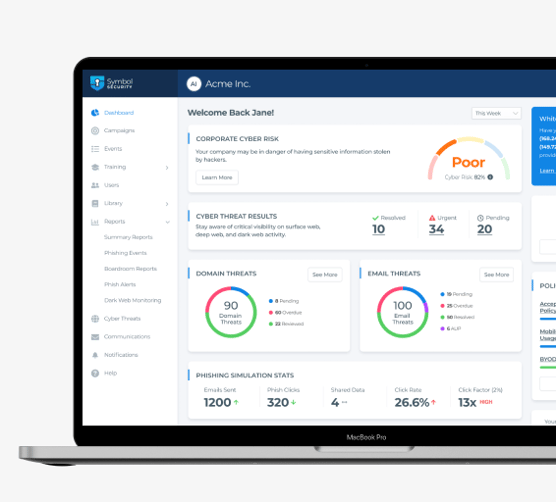
Symbol’s application then engages users to remediate and fix their stolen credential vulnerabilities. Finally, Symbol reports on all user and administrator remediation efforts on a real-time basis ensuring that these vulnerabilities are documented and fixed. Human vulnerability identified, human vulnerability remediated.